14 Jun 7 Growing Cyber Security Threats to Take Note of in Singapore

As a growing smart nation, Singapore is no stranger to threats of a digital kind. The country has had its fair share of cyber attacks, including some high-profile data breaches. Below, we’ve listed the 7 types of growing cyber threats in Singapore, to take note of this 2019.
1. IoT Attacks

The “Internet of Things” is a term that is becoming more and more popular these days. But what does this term mean exactly? According to Forbes, the “Internet of Things” simply put, is the concept of connecting devices that have an on or off switch to the Internet. And to other devices. Examples of devices that belong to the “Internet of Things” include handphones, your computers, and laptops.
Nowadays, more and more devices have the ability to connect to the internet. And the list will continue to expand. It is estimated that by 2020, there will be close to 31 billion connected devices. It’s obvious that there will be an increase in IoT attacks.
Once a hacker takes charge of an IoT enabled device, they’ll have access to a number of different devices. This can be used to wreak havoc for unlawful financial gain.
2. Cryptojacking

Cryptojacking refers to the unauthorized use of someone’s computer in order to gain access and mine cryptocurrency (e.g. Bitcoin). Much like phishing, hackers and cybercriminals gain access to someone’s computer using malicious links distributed in unsuspecting emails.
The most terrifying aspect of crypto jacking is that it requires little to no skills. In fact, crypto jacking kits are available on the Dark Web for as little as US$30. Earlier in January 2018, researchers discovered that the Smominru crypto mining botnet infected close to half a million devices.
With cryptocurrencies like Bitcoin slowly gaining mainstream popularity. As such, users can expect crypto jacking attacks to be more popular and prevalent both in Singapore and other nations with established digital landscapes.
3. Mobile Malware

Everything’s on mobile these days. You can use your phone for transportation services, and even make cardless payments through apps. With more and more users choosing to store personal data in their mobile phones, it’s no wonder that cybercriminals are now targeting phones.
Mobile Malware is a threat that has been distributed at a massive scale. Around 150 million Android phone users were affected by Simbad, a mobile malware that hides within advertisements in games. Investigations show that Simbad was found in more than 200 mobile applications (apps) found in the Google Play Store.
Other creative forms of mobile malware distribution include infection via images. Unfortunately, due to an Android bug, a standard photo file can turn into a vehicle for a Malware infection. Thankfully, Google has fixed the issue. However, there is no telling if there will be other creative forms of malware strains that will crop up in the near future. With an alarming number of infected users, security decision-makers can no longer dismiss mobile malware threats.
4. Threats to Industrial Control Systems (ICS)

ICS, short for Industrial Control Systems, is any device, instrument, network or software that is used to operate or automate industrial processes. You can think of them as the industrial Internet of Things (IoT). ICS are devices that connect to other sensors or devices through the internet, which can increase the potential of an attack.
Threats to Industrial Control Systems include Malware attacks, through portable media including USB sticks, DVD’s, smartphones, and even cameras. Once a Malware infection has been established, it is able to bypass any established firewall and connect back to the attacker. This allows the virus to either:
- Download additional Malware viruses
- Leak sensitive ICS information to the attacker
Without a strong defense strategy, Industrial Control Systems can also be infected through other means.
5. Phishing

Cybercriminals often use fake websites designed to look like a particular service, to phish users. The aim of phishing is to trick users into giving in their name and login details.
In Singapore, there has been a stark rise in the number of sophisticated phishing attacks since 2018. To help you understand the jump, let’s put in the numbers. More than 2,000 phishing URLs with Singapore links were found in 2016. However, in 2017, more than 23,000 phishing URLs were discovered. Additionally, according to a report by the Today paper, both malware infections and website defacement were also on the rise.
One way to avoid phishing is by educating your employees. Find out what employees should look out for in the article, “Yes, Cyber Security Should Matter to HR Personnel too!”.
6. Website Defacement
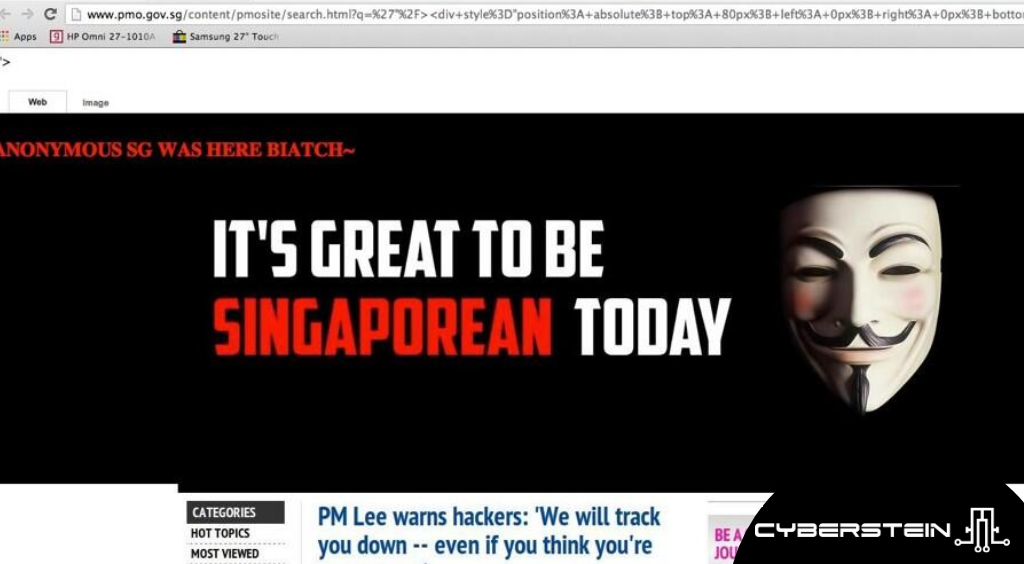
Website defacement occurs when the visual appearance of the site or a web page has been altered. Typically, website defacement features company logos, text, or web pages either replaced or altered. The motive of website defacement is either for fun or to protest the message the site is promoting (i.e. hacktivists).
As web defacement takes significantly less effort than other more complex forms of cybercrime, it is on a steady rise. In Singapore, the main targets of web defacement include SMEs based in the manufacturing, retail, and information technology sector.
Web defacement might seem harmless but they do have multiple unsavory implications. The most noticeable consequence of a defaced website is the damage it causes to your company’s reputation. As web defacement involves small, minute changes, it might take a while for your company to detect it. Exposing the altered content to hundreds or thousands of your daily visitors. This, combined with social media, might cause further damage to your company’s website.
7. DDoS Attacks
DDoS is short for “Distribution Denial of Service”. The aim of this attack is to overwhelm its target and to disrupt the normal traffic of a website. Think of DDoS attacks as a traffic jam, it prevents you and your vehicle to reach the appropriate destination on time. These type of attacks can be divided into three categories:
- Application layer attacks (e.g. HTTP floods)
- Protocol attacks (e.g. SYN flood)
- Volumetrics attacks (e.g. DNS amplification)
DDoS attacks have been around for a while. However, experts predict that these attacks will gain more popularity in 2019. Learn more about DDoS and the different categories of attacks here.
Your First Line of Defense … Matters
Expect a number of cybersecurity threats to emerge in Singapore’s digital landscape this 2019. Here at Cyberstein, we offer the best manpower available to act as your first line of defense. Find out more about Cyberstein’s services here. Or contact Victor at ([email protected]) for more information on how outsourcing and recruiting temporary cybersecurity talents is a great option to consider when it comes to protecting your company, its resources, and reputation online.
Stay informed, follow A Very Normal Company on Linkedin for more news and updates on Cyber Security outsourcing and recruitment in Singapore.


