
22 Nov How HR Can Become the Biggest Loophole in a Secure Organization

The key to having good cybersecurity is HR. Human resources handle some of the most sensitive data in the organization (e.g. personal data). Which is why it is crucial for the HR department to keep itself secure for the organization.
Here are some of the reasons why your HR team can be your worst enemy when it comes to cybersecurity:
1. Mishandling Login Credentials
To the untrained eye, the HR team might only be directly responsible for an employee’s login credentials whenever an employee enters or leaves the organization. However, it is also the HR team’s responsibility to both train new employees and re-train current employees on safe and secure ways to handle login credentials. It should go without saying that poor login credentials and not using a multi-factor authentication for logins can lead to data breaches.
Learn more about the importance of password protection to HR teams here.
2. Mishandling Personal Data

Hackers and cybersecurity criminals love personal data. Sometimes they still personal data just to hold it for ransom and earn money.
Other reasons why cybercriminals love personal data include:
- Identity theft: This is a goldmine for hackers. For instance, personally identifiable information (i.e. data that can be used to identify, locate, and contact an individual).
- Use your infrastructure: It’s expensive to store data. Some hackers hack just because they want to use your internal storage and servers instead of paying for their own.
- For fun: Sometimes, there’s just no reason why hackers choose to hack. These criminals are not motivated by monetary gain, which could make things harder for organizations to respond to. To these hackers, the idea of taking down the defenses of an established and well-known company is alluring.
3. Lack of Cybersecurity Education

Education instead of awareness training needs to be at the forefront of cybersecurity. It is up to the HR team to step up and lead the cybersecurity culture amongs executive employees. In the words of Derek Bok, former president of Harvard University once said, “If you think education is expensive, try ignorance”.
According to the SANS Institute, 95% of all attacks on enterprises are the result of successful spear phishing. Basically, spear phishing is an email scam sent out by cybercriminals in order to steal data. An example of a phishing email can be seen below:
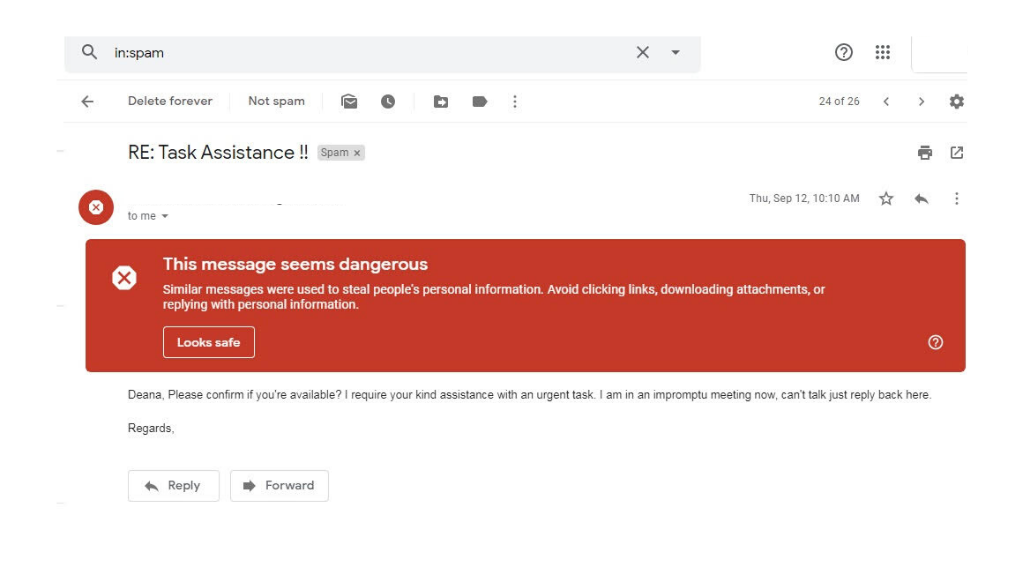
As an HR executive, your goal is to educate employees about common threats much like spear phishing. We recommend working with a designated cybersecurity or tech specialist to find easy ways to protect and educate your employees, to create short, easy to remember infographics!
Furthermore, your organization’s chances of being phished is lowered to only 5% when employees are trained.
A survey by Cloudmark found that C-Suite executives are often the primary targets of phishing attacks. However, even random targeting can provide invaluable opportunities for phishers to gain entry into the organization and access to data. Every employee has the potential to breach data and the risk increases steadily, the bigger the company is.
4. Not Planning a Data Breach Plan

Sometimes protection is not always enough. Which is why organizations securely protected or not should always prepare a contingency plan. Of course a data breach plan should involve more than just the HR team.
In fact, it should include members in the following departments:
- IT and Tech
- Legal
- Human Resources
- Public Relationship
- Customer Care
- Leadership
However, the HR team will have to identify and map out its responsibilities should an attack happen. These responsibilities could include; notifying employees of the breach, as well as creating and circulating the frequently asked questions.
5. Failing to Develop Practical Cybersecurity Policies

Many organizations forget that both cybersecurity specialists and hr professionals will need to work together to develop a cybersecurity plan. The role of the hr team would be to ensure that the policies and measures are ethical and practical enough to be carried out.
Some examples of cybersecurity policies include:
- Develop a system for employees to report stolen or damaged equipment as soon as possible.
- Blocking suspicious websites from computers in the office. Learn more about the detrimental effects unsafe online habits have on the company here.
- Hold teams and individuals accountable when they download suspicious, unauthorized, or illegal software on their company equipment.
- Encourage 2 Factor Authentication login for all passwords.
6. Failing to Identify High Risk Employees

Think that employees with lesser access have less opportunities to cause data breaches? Think again! An estimated 27% of cyber attacks are caused by human error.
Employees with terrible internet habits need to be monitored and labelled as “high risk” employees. Data breaches can occur when a careless employee leaks unsuspected information freely on social media.
Recommended Reading: Meet Gen Z: Your Organization’s Biggest Cybersecurity Threat
Alternatively, an internal data breach can occur when a cyber criminal impersonates a member of the organization to gain access to data. Known as ‘spoofing’, these attacks are quite common in banking and tech companies. In Singapore, up to 90% of companies in the banking, financial services, and tech trade have experienced either a spoofing attack or an attempted spoofing.
Data breaches cost companies a lot of money (see image). Breaches threaten your branding – one of the most important assets to any company. Google +, a social network service operated by Google is a good example. The service was forced to shut down after a security bug allowed hackers to access over 400,000 different profiles. Which goes to show you just how perilous a data breach can be.
With a wealth of sources available to learn cybersecurity from, excuses such as little to no training and lack of cybersecurity awareness are no longer valid. Especially when these excuses lead to the exposing of organizations and the sensitive data they are supposed to be protecting.
Did you find this article useful? Let us know in the comments section below!
Outsource your cybersecurity headache to trained tech recruiters with A Very Normal Company. At A Very Normal Company, we offer the best manpower available to act as your first line of defense. Find out more about A Very Normal Company here. Or contact Victor at ([email protected])for more information on how outsourcing and recruiting temporary cybersecurity talents is a great option to consider when it comes to protecting your company, its resources, and reputation online.
Stay informed, follow A Very Normal Company on Linkedin for more news and updates on Cyber Security outsourcing and recruitment in Singapore.
Read More: HR Professionals: Here’s What Your IT Hiring Manager is Trying to Tell You

